What Happened?
Over the past few weeks there has been an increase in phishing scams targeting U.S Postal Service (USPS) Customers by Iran-based threat actors (according to Domain-Tools Researchers). Here is a brief coverage on the extensive SMS phishing operation that tries to steal personal and financial info by spoofing USPS, as well as other National postal services from other countries.
Recently covered by KrebsOnSecurity( being Mr. Brian Krebs himself a previous writer for the Washington Post.), and some early warning signs from the U.S. Postal inspector about a month ago, a reader who received an SMS purporting to have been sent by the USPS, saying there was a problem with a package destined for the reader’s address. Clicking the link in the text message brings one to the domain “usps.informedtrck[.]com.”
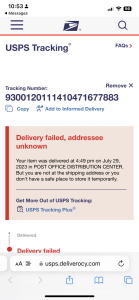
The landing page generated by the phishing link includes the USPS logo and says “Your package is on hold for an invalid recipient address. Fill in the correct address info by the link.” Below that message is a “Click update” button that takes the visitor to a page that asks for more information.
The remaining buttons on the phishing page all link to the real USPS.com website. After collecting your address information, the fake USPS site goes on to request additional personal and financial data.
Some Examples:
This phishing domain was recently registered and its WHOIS ownership records are basically nonexistent. However, we can find some compelling clues about the extent of this operation by loading the phishing page in Developer Tools, a set of debugging features built into Firefox, Chrome and Safari that allow one to closely inspect a webpage’s code and operations.
Listed below are some of the domains linked to the USPS links by the Threat actors involved.
usps.receivepost[.]com
usps.informedtrck[.]com
usps.trckspost[.]com
postreceive[.]com
usps.trckpackages[.]com
usps.infortrck[.]com
usps.quicktpos[.]com
usps.postreceive].]com
usps.revepost[.]com
trackingusps.infortrck[.]com
usps.receivepost[.]com
usps.trckmybusi[.]com
postreceive[.]com
tackingpos[.]com
This information was confirmed by the address link for the Krebs reader, via URL.Scan.io which is a useful tool for proving the validity of some domains and showcases the slew of many other domains in association to the ones listed.
Other nations have also been affected by this phishing scam through similar means and assumed Threat actors are listed below:
The Australia Post, An Post (Ireland), Correos.es (Spain), the Costa Rican post, the Chilean Post, the Mexican Postal Service, Poste Italiane (Italy), PostNL (Netherlands), PostNord (Denmark, Norway and Sweden), and Posti (Finland).
A 3 part solution:
- Being able to spot a phishing attack as its being presented to you, remember that USPS and other postal services would not shoot you a text or email requesting your financial information much less home address without it becoming a phone call.
- Spotting a spoofed website or phishing links, https://www.usps.com is a valid site link that is not spoofed and when you go to the site link in the search bar you usually will see a Lock on the top left. This means that it is a generally secure domain. http://unitedstatespostalservice.com, now if you were to get a link like this, you should know before even clicking on it, the validity isn’t there, it may be spelt out, it may have an additional number or characters, but its not the link to the real website. This is a tell-tale sign of site spoofing.
- The last part of the solution is either to call USPS or the postal service and question them to confirm if they had reached out in regards to the reason via email or text. As well as using a tool such-as URLScan.io, IPqualityscore’s malicious URL scanner or ScamAdviser.


