In July 2023, Microsoft’s mailing infrastructure was breached during the “Storm-0558” attacks that were attributed to Chinese hackers, who have been called state-linked to the PRC by Microsoft and U.S. officials. During the attack, it has now been confirmed by a Senate staffer that the hackers gained access to email services belonging to at least ten State Department workers, where reportedly 60,000 emails were stolen, and additionally, those breached included the accounts of the U.S. Ambassador to China, the Secretary of Commerce, the Assistant Secretary of State, and others at 25 organizations in total, encompassing but not limited to the U.S. Commerce Department and accounts focused on Indo-Pacific diplomatic relations. The Chinese government has denied the U.S. claims that the hackers were linked to the state, calling the allegations that it stole emails “groundless narratives”. The confirmation of the quantity of information stolen was only revealed recently regarding the ten State Department accounts mentioned before; however, hundreds of thousands of other emails and files are thought to have been compromised by the exposing attacks, which ranged to a number of organizations still unnamed.
Microsoft released two statements, one mid July following the attacks in which analysis is done on the Storm-0558 techniques for unauthorized email access, and then a later one in early September wherein Microsoft explains how the cryptographic key was stolen from an engineer working for them, and how it was leveraged to access accounts it shouldn’t have been able to. The company claims the flaws have been fixed that allowed the key being accessible, a rep said the account had been hit with a “token-stealing malware” but didn’t provide further details at the time.
“Unanswered Questions in Microsoft’s Response:
First, how did the attacker get the crash dump in the first place? Buried in Microsoft’s description is this line (emphasis added): “the Storm-0558 actor was able to successfully compromise a Microsoft engineer’s corporate account.” Re-read that. The attacker compromised a Microsoft employee’s account—presumably one that was protected with MFA and conditional access policies—and that compromise gave them access to the crash dump. The dump was generated in April 2021. Microsoft’s recap says that attacks started on May 15, 2023, but they also cite attack activity patterns starting in April 2023 so it’s hard to tell when the attacks truly began.
That’s a two-year period in which Microsoft’s vaunted internal security controls apparently failed to notice the Chinese government rooting around in their network.
Second, how did the attackers know to find the crash dump? Microsoft said that they didn’t have enough log data to definitely prove that the attacker stole and exfiltrated the crash dump, because they don’t retain logs for long enough. If they have any evidence indicating what else the attacker did, they aren’t saying so, but I am betting that because of the time span of the attack, they do not have that evidence.
Third, what else did the threat actor have access to during that time period? One of the reasons that advanced persistent threats (APTs) are so hard to deal with is that they establish persistence—and the longer they’re in a network, the more difficult it is to ensure that you’ve removed all of their points of presence and persistence.
Practical Actions to Stay Safe:
The fatalists among us might be tempted to shrug and say “Well, if Microsoft gets hacked, what chance do I have?” That attitude ignores the fact that you’re probably not going to be targeted by the Chinese government and that there are some practical steps you can take to reduce your risk.
First, are you appropriately applying MFA and conditional access policies? Are the correct policies being applied, consistently, to the correct set of users? Can you demonstrate that?
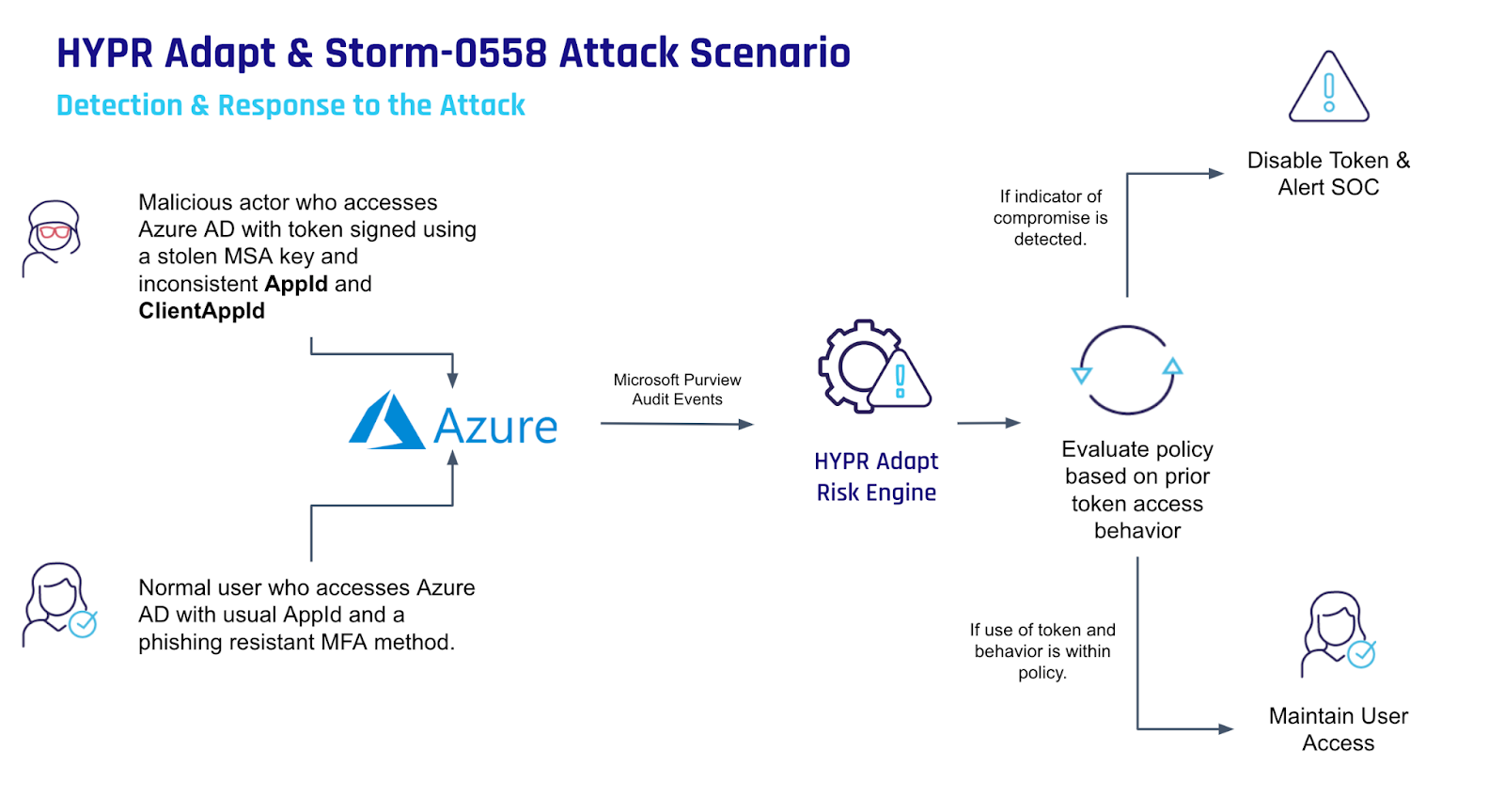
Second, how’s your logging? Some of the organizations attacked by Storm-0558 didn’t notice because they didn’t have the MailItemsAccessed event enabled because that costs money. Mailbox auditing is available for all Exchange Online customers, but ingestion of mailbox audit data into the unified audit log is only for Office 365 E3 and above. The MailItemsAccessed event used to be available for Office 365 E5 and above, but now (deployment to tenants starts in September 2023) it’s available for Office 365 E3.
If you haven’t enabled MailItemsAccessed for logging, or aren’t sure if you do, you should enable it ASAP. That event is the key indicator that an application, authorized or not, has accessed items in an Exchange mailbox. The original attacks were detected when the target organization (a Federal Executive Civilian Branch agency) noticed an unusual application ID had generated MailItemsAccessed events in their audit logs. If you have other sensitive data items, users, or network resources, you should ensure that you’re logging the right things for them, but also that you have the appropriate detection and review mechanisms in place to catch exceptions.
Analysis of audit data can be done through systems like Splunk or Sentinel. Microsoft recently changed the way that the Search-UnifiedAuditLog cmdlet works, so make sure that the data flowing from the unified audit log into your data repository is complete and accurate. You could also use the technique explained in this article to monitor events added to the unified audit log for inconsistencies. Whatever tools you use to capture and analyze audit data, make sure that events are reviewed.
Third, how easy would it be for an attacker to move laterally into (or out of) any protected networks you maintain? The idea of having an isolated production network is well accepted in the industry, but as soon as you start allowing users or data to move from that isolated network to other less-isolated networks, you’ve created a potential vulnerability of which you should be both mindful and cautious. You should verify that you have appropriate security controls, adequately enforced, along with logging and alerting to monitor movement between these networks.
More Attacks Coming
We haven’t seen the last of nation-state-sponsored attacks, nor have we seen the last of the impact of this particular attack. While we wait to see what embarrassing revelations come next, spend some time investigating the three items I mentioned above to help protect yourself in the future.”


